0x00 影响范围
|
|
0x01 搭建wordpress
|
|
浏览器访问
0x02 下载Social Warfare插件
|
|
浏览器访问:
|
|
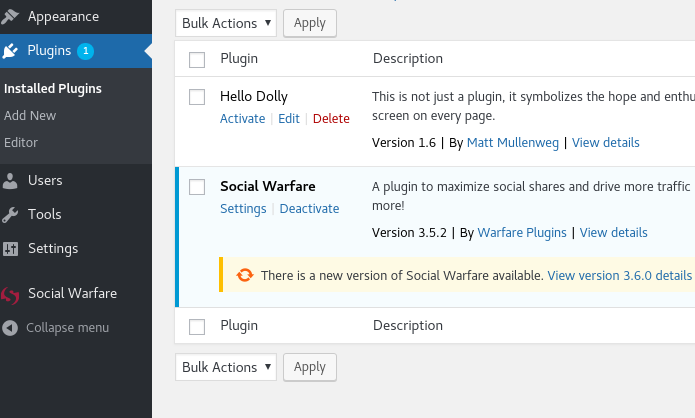
登进后台后部署插件,选择social warfare后点击Activate:
左侧多出插件设置:
0x03 漏洞复现
在攻击机的Web根目录部署payload
(tips: centos6开启httpd后,关闭iptables服务)
|
|
浏览器访问能看到:
|
|
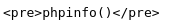
构造URL并访问:
|
|

复现成功
|
|
|
|
浏览器访问

|
|
浏览器访问:
|
|
登进后台后部署插件,选择social warfare后点击Activate:

左侧多出插件设置:

在攻击机的Web根目录部署payload
(tips: centos6开启httpd后,关闭iptables服务)
|
|
浏览器访问能看到:
|
|
构造URL并访问:
|
|

复现成功